This Blog is dedicated Digital Forensics and Incident Response, tools, techniques, policies, and procedures.
Tuesday, November 16, 2010
Sniper Forensics Videos!
If you have not had a chance to see either of the Sniper Forensics talks, now is your chance to download the videos or the slide decks!
Wednesday, October 27, 2010
Sniper Forensics 2.0 Tools, Links, and Commands
Thank you for attending my talk! I hope you get out of it as much I put into it!
Happy Hunting!
Tools
====
F-Response (http://www.f-response.com/)
Memoryze (http://www.mandiant.com/products/free_software/memoryze/)
Audit Viewer ( http://www.mandiant.com/products/free_software/mandiant_audit_viewer/)
UnxUtils (http://sourceforge.net/projects/unxutils/)
Grep (http://gnuwin32.sourceforge.net/packages/grep.htm)
TextPad (http://www.textpad.com/download/)
Case Notes (http://www.qccis.com/forensic-tools)
The Sleuth Kit (http://www.sleuthkit.org/sleuthkit/download.php)
Log2Timeline (http://log2timeline.net/)
SIFT Workstation (https://computer-forensics2.sans.org/community/siftkit/)
AnalyzeMFT (http://www.integriography.com/)
RegRipper (http://regripper.net/?page_id=150)
RipXP (http://regripper.net/?page_id=150)
FTK Imater 3.0 (http://www.accessdata.com/downloads.html)
Syntax
=====
Use these commands to rip registry hives.
C:\tools\RegRipper\rip.exe –r c:\cases\customerX\registry\SAM –f SAM > c:\cases\ripped\systemY_sam_ripped.txt
C:\tools\RegRipper\rip.exe –r c:\cases\customerX\registry\system –f System> c:\cases\ripped\systemY_system_ripped.txt
C:\tools\RegRipper\rip.exe –r c:\cases\customerX\registry\ntuser.dat –f ntuser> c:\cases\ripped\systemY_ntuser.dat.userX_ripped.txt
Use these commands to create a bodyfile and timeline. If you want a more detailed explanation of how to generate timelines, read my blog posts about timeline creation.
C:\tools\TSK\fls –m ‘C:/’ –f ntfs –r \\.\F: > c:\cases\customerX\timelines\systemY_bodyfile
Perl C:\tools\TSK\mactime.pl –d –b C:\cases\customerX\timelines\systemY_bodyfile\systemY_timeline.csv
You can add logs to your bodyfile with Log2Timeline
C:\>Perl C:\Perl\bin\Log2timeline –t
You can hives and NTUSER.dat files to your bodyfile with regtime
C:\>Perl C:\tools\bin\regtime.pl –m HKLM/system –r c:\cases\customerX\hives\system >> \c:\cases\customerX\timelines\systemY_bodyfile
Search for suspect keywords
C:\cases\customerX\ripped>strings *.txt | grep –i
C:\cases\customerX\timeline>strings *.csv | grep –i
Search for suspect timeframe
C:\cases\customerX\ripped>strings *.txt | grep –i
C:\cases\customerX\timeline>strings *.csv | grep –i
Know how to stack your searches! CRITICAL!!!
Grep –i
Grep –i
Sunday, October 24, 2010
SecTor 2010 - Debuting SF2

I will be debuting the second version of Sniper Forensics, titled, "Target Acquisition" at SecTor in Toronto, Ontario, Canada on October 27th. It's a great conference and I couldn't be more excited!
Here are some quotes about what others are saying about SF2!
“As environments continue to grow in size and complexity, incident response teams entrenched in the “image everything” methodology will find themselves not able to understand the situation as fast as the threat is evolving within a target environment. Adopting the Sniper Forensics Methodology, will decrease the cost of the investigations while providing results many times faster over traditional approaches when applied to modern environments.”
- Nicholas Percoco
Senior Vice President, Trustwave SpiderLabs
=============================
“If you have a specific goal, you are much more likely to achieve it. Knowing what you want out of an investigation, before you start, will help you know when you're finished.”
- Jesse Kornblum
Computer Forensics Research Guru, Kyrus Technology
=============================
"Using F-Response as part of the "Sniper Forensics" model is the perfect logical extension of our original mission. Get answers, not just information."
- Matt Shannon
Founder, F-Response
=============================
“'Sniper Forensics: Target Acquisition' walks up to an analyst and slaps him right in the face! Here are targeted tools and techniques, straight from successful field ops, that every analyst needs to know! Once you've defined your target, go grab the data you need, and optimize your time and resources to get the job done!”
- Harlan Carvey
Vice President of Advanced Technical Projects, Terremark Worldwide
Author of “Windows Forensic Analysis 2nd Edition”
Author of the Blog, “WindowsIR.blogspot.com”

Saturday, October 23, 2010
The “Not So” Perfect Keylogger
Below, is a timeline excerpt from a case I was working recently in which I saw Perfecet Keylogger running natively (ie…under the default naming convention). It should be noted, that the means of infiltration in 99% of these cases in an open remote administration port and default administrative passwords. This gave the intruders an easy path onto the target systems, and the credentials necessary to install the malware.
Pay special attention if you will, to the file names besides bpk.exe, specifically the letters after the “k” in “bpk”.
F:\timelines>strings _timeline.csv | grep -i bpk
Fri Aug 21 2009 02:42:56,499712,m..b,r/rrwxrwxrwx,0,0,13919-128-3,'C:/'/WINDOWS/system32/bpk.exe
Fri Aug 21 2009 02:42:56,19456,m..b,r/rrwxrwxrwx,0,0,13920-128-3,'C:/'/WINDOWS/system32/bpkr.exe
Fri Aug 21 2009 02:42:56,19968,m..b,r/rrwxrwxrwx,0,0,13922-128-3,'C:/'/WINDOWS/system32/bpkhk.dll
Fri Sep 04 2009 01:12:50,188895,ma.b,r/rrwxrwxrwx,0,0,14008-128-3,'C:/'/WINDOWS/security/bpk.chm
Mon Oct 19 2009 07:02:03,623,ma.b,r/rrwxrwxrwx,0,0,13996-128-1,'C:/'/WINDOWS/system32/bpk.dat
Sat Aug 21 2010 02:43:06,22586,...b,r/rrwxrwxrwx,0,0,13923-128-4,'C:/'/WINDOWS/Prefetch/BPK.EXE-06BA93D1.pf
As you can see, some of the key file names associated with Perfect Keylogger are: bpk.exe, bpkr.exe, bpkhk.dll, bpk.dat, and the configuration file not listed in the first timeline excerpt, pk.bin. These files are normally found in the C:\Windows\System32 directory, but can really run from any custom location, as indicated by the second timeline excerpt. When it’s seen in a RAM dump, it looks like this:

Below is a second example, in which the naming convention has been changed to confuse the would be investigator. Look at the letters after the “t” in “wuault.exe”. Do they look familiar? They should!
F:\timelines>strings timeline.csv | grep -i wuault
Fri Sep 04 2009 01:34:51,438272,m..b,r/rrwxrwxrwx,0,0,14055-128-3,'C:/'/WINDOWS/security/wuault.exe
Fri Sep 04 2009 01:34:51,24576,m..b,r/rrwxrwxrwx,0,0,14056-128-3,'C:/'/WINDOWS/security/wuaulthk.dll
Fri Sep 04 2009 01:34:51,40960,m..b,r/rrwxrwxrwx,0,0,14059-128-3,'C:/'/WINDOWS/security/wuaultwb.dll
Fri Sep 04 2009 01:34:51,215040,m..b,r/rrwxrwxrwx,0,0,14060-128-3,'C:/'/WINDOWS/security/wuaulti.dll
Fri Sep 04 2009 01:34:51,7680,m..b,r/rrwxrwxrwx,0,0,14061-128-3,'C:/'/WINDOWS/security/wuaultr.exe
Sat Sep 04 2010 05:44:06,16674,...b,r/rrwxrwxrwx,0,0,13976-128-4,'C:/'/WINDOWS/Prefetch/WUAULT.EXE-0E3FBF35.pf
When captured in a RAM dump, it looks like this:

Notice that the path is C:\windows\security. Also of note, look at the timeline above…see the “birth” date in my timeline? It says “Fri Aug 21 2009 02:42:56”, but the first prefetch file shows a timestamp of, “Sat Aug 21 2010 02:43:06”. About 10 seconds later…exactly one year later? What’s up with that? Well…let me tell you, but first, let’s quickly go over the Master File Table ($MFT), specifically the Standard_Information ($S_I), and File_Name ($F_N) attributes.
REAL basically, we all know that the $MFT holds information about the files on the disk. Well, one of those attributes, the $S_I, is accessible by the operating system (OS) and the user. So, what…that means that they can be changed, accessed, and yes…stomped. BUT, the $F_N attribute is not touched by anything except the kernel. So what does that mean? It means no modifications by the OS or the user…ie…no stomping.
So, Harlan sent me a Perl script he wrote which goes through the $MFT and extracts and parses the $S_I and $F_N attributes. So with our friend bpk.exe, it would look like this:
13919 FILE 14 1 0x38 4 1
0x0010 96 0 0x0000
0x0000
M: Fri Aug 21 07:42:56 2009 Z
A: Tue Oct 19 16:24:13 2010 Z
C: Tue Oct 19 16:12:26 2010 Z
B: Fri Aug 21 07:42:56 2009 Z ← This is the “modified” birth date of the file on the system.
0x0030 104 0 0x0000
0x0000
FN: bpk.exe Parent Ref: 847 Parent Seq: 1
M: Sat Aug 21 07:42:56 2010 Z
A: Sat Aug 21 07:42:56 2010 Z
C: Sat Aug 21 07:42:56 2010 Z
B: Sat Aug 21 07:42:56 2010 Z ← This is the actual “birth” date of the file on the system.
0x0080 88 1 0x0000
0x0000
And…it matches our Prefetch file, which further supports our finding that the timestamps have been modified. So be wary…if you come across Perfect Keylogger in a case, it will be offset by one year – I have seen this to be true in every Perfect Keylogger case I have worked, and it seems to be done as part of the install script. Now, while I have seen the binaries and associated dlls renamed, I have not seen the dump file (bpk.dat) or the configuration file (pk.bin) renamed. After downloading a trial version of Perfect Keylogger, I can see that you can change the output file, and path, so it’s possible…but like I said…just never seen it. I’m not certain the same can be said for the configuration file. I have tried several times unsuccessfully, so I think it may be hard coded into the program.
So if you try to open the bpk.dat, and the pk.bin they appear to be encrypted. Or are they? Through the efforts of the SpiderLabs Research Team, we found that they are NOT really encrypted, but rather encoded with a single xor key, 0xAA. So, when you use a simple xor script, against either one, you may get something that looks like this (since this was from a real case, I have modified the output, but the methods and the output format looks the same):
PK Password: "y0uv3b33np0wn3d"
License Name: "www.hacked.ws"
License: "PGTDFADBEPRCHGB"
Email Enabled?: true
SMTP Server: "10.10.10.10"
SMTP Port: 25
SMTP Username: "user"
SMTP Password: "p@ssw0rd"
Email Address: "p0wn3d@hackmemail.com"
FTP Enabled?: false
Hotkey Hex: keycode=0xdc modifier=0x07
Key-combo: SHIFT + CTRL + ALT + 6
So, this is great! You have the attacker’s email, the server he was using, his username and password! Better yet, you have the key-combo which is used to bring the Keylogger out of hidden mode. If the attacker wanted to use FTP instead of SMTP, you would see the same type of login information as you do for the SMTP example provided above. If you know that it’s running, but you don’t see the icon in the bottom of the screen, it’s in hidden mode. Simply use this key combination, and BAM, the icon will suddenly appear! Then, simply enter in the “PK Password” and you have access to the admin console of the keylogger! This configuration file will give you access to the time intervals in which the dump file is emailed or FTP’d. Pretty slick eh!
Now, it also uses the same xor to encode the dump file! So if you run the same xor script, you may see something that looks like this:
F:\ >cat bpk.dat.out
06-09-2010 03:22
wuault.exe
BlazingTools Perfect Keylogger: Options
[Password captured: p@ssw0rd]
15
$#$#$#$#$#$#$#$#$#$#$#$#$#$
19-10-2010 10:53
Explorer.EXE
Run
cmd
$#$#$#$#$#$#$#$#$#$#$#$#$#$
19-10-2010 10:54
cmd.exe
C:\WINDOWS\system32\cmd.exe
d:
dir
mkdir images
cd im
$#$#$#$#$#$#$#$#$#$#$#$#$#$
19-10-2010 10:56
cmd.exe
C:\WINDOWS\system32\cmd.exe
mkdir vol
Nice! Note that if you don’t have any scripting-fu (Perl, Ruby, Python, etc) you can simply install the trial version of Perfect Keylogger in a vmimage, and use the “view the log” option to see the decoded versions of the logs.
Additionally, the only registry entries I have seen for Perfect Keylogger are in the UserAssist key of an ntuser.dat file, showing initial execution, and in the RUN key of the SOFTWARE hive, showing that it’s set to start up at reboot.
NTUSER.DAT – UserAssist Key
=========================
UEME_RUNPATH:C:\Documents and Settings\
Software Hive
=========
Software\Microsoft\Windows\CurrentVersion\Run
C:\P15xx\DisableWriteCache.exe -s all
"C:\Program Files\UltraVNC\WinVNC.exe" -servicehelper
C:\WINDOWS\System32\bpk.exe ← Indicates that the keylogger will start each time the system boots.
So, if you are working on a case and you expect that you may have Perfect Keylogger, here are the key indicators of compromise:
Presence of:
• pk.bin, or bpk.dat (configuration or dump files)
• bpk.exe, wuault.exe, wuauclt.exe (running from the incorrect directory)
• binary and dlls timestopmed (check the $MFT)
• Entries in the ntuser.dat and SOFTWARE hives
• Active process running RAM with the same ending letters (as seen in the timeline example)
You can decode the configuration file and dump files with a simple xor, 0xAA key. Alternatively, you can use the demo version of the keylogger itself to open the dump file.
Good luck, and happy hunting!
Tuesday, October 12, 2010
Call for quotes
Thanks!
Friday, August 27, 2010
Court Approved?
THERE IS NO SUCH THING AS COURT APPROVED TOOLS.
Saying that one tool is court approved and another is not, is like saying you can take crime scene photos with a Nikon, but not a Kodak. It's just silly, and it's a myth perpetuated by those who seek to benefit from the existence of such a rumor.
Now, there ARE tools that have been used in court cases, which may be more familiar to attorneys and/or judges. This does NOT make them court approved, it simply means that they have been used before...nothing more. Pay careful attention to what I am writing here...simply using a tool...any tool...DOES NOT make your findings any more relevant, valid, or indisputable then if you had used any other tool to come to the same conclusions. The data is simply the data.
Your job as a forensic investigator is to produce forensically sound results. This too is a term that is often used incorrectly or as a buzz word. Forensically sound means that if given the same set of data, any other investigator, using any other tool, would come to the same conclusion.
Now really think about what this means. Let's say you have been asked to identify a date range for files in a specific directory. If given the same image, 10 different people, using 10 different tools, should come to the exact same results...EnCase, FTK, TSK, MFL, Perl scripts, Python, whatever...the conclusion should be the same because the means by which you would extract that data is the same.
The implications of a conclusion being forensically sound invalidate the entire premise of something being court approved. How can one tool that comes to the same conclusion as another tool be approved while the other is not? They DO the same THING. While the GUI may change, or the vendor - open source code versus proprietary - Linux versus Windows...it doesn't matter. The data is the data.
Thursday, August 5, 2010
Surgery!
She is OK now, an at home recovering, but obviously my focus had to shift from forensics to my family. Once she is back on her feet and feeling better, I will be back to my usual forensic-y goodness.
I also want to give a HUGE thanks to all of you from BSIDES and SANS for sending me your thoughts and prayers. I also want to issue s public apology to the folks at The Next HOPE conference and DEF CON for having to miss my speaking engagements. You have my most sincere apologies, and hope you realize that my absence was a significant medical issue.
Thanks again!
Sunday, July 11, 2010
SANS What Works 2010 - HUGE Success
The Conference once again had some of the best speakers in the world of incident response and forensics including, Major Carol Newell of the Broken Arrow, OK Police Department, Rob Lee, Harlan Carvey, Jesse Kornblum, Troy Larson, Kris Harms, and Robert Shullich.
This is the second year for the conference, and I think that without question, the conference continues to improve. In a field as dynamic and fluid as Incident Response and Computer Forensics, investigators really need to keep current with not only their skill sets, but with emerging technologies, theories, and methodologies. This only makes sense, since the "bad guys" we are all trying to catch, are undoubtedly doing the same thing! This is crux of the summit, and the true value add for the attendees...you get to hear and see what is ACTUALLY working from some of the best minds in the industry.
The major focus this year was on the new challenges we face with the arrival of Windows 7, which is very different than XP, and Vista. There are new registry entries, gobs of new event logs, and a new file system layout. All in all, it going to mean countless hours of research by investigators to be efficient and effective at performing comprehensive forensic investigations.
The other big takeaway from the conference is the involvement with corporate investigators with law enforcement agencies...something I am a HUGE advocate of! Look for a LOT MORE of this to come, but the gist is this...LE agencies do not use police for forensic pathology, or for forensic dentistry, or forensic arson investigations. Why would they? For this, they would use doctors, dentists, and fireman. Why? Because they are subject matter experts in those fields. Why then, when it comes to computer forensic (arguably one of the most difficult of the forensic sciences - based on the vast array of digital media current in use by the "average" person) do LEs want to keep these types of investigations in house? Why not treat cases involving digital media, the same way they would any other case involving a forensic scientist, and seek the assistance of subject matter experts? This is the direction we want to start moving.
If you are an investigator, and want to start helping in LE cases, here are a few tips from Major Newell:
1. Certifications...get them! They look great on the stand, and will help you with the vetting process by the PD and as an expert witness.
2. Be presentable. You don't have to be a cover model by any stretch...but you ARE going to be representing the PD or the DA's office. Dress accordingly!
3. Letters of recommendation. Get these from any law enforcement agency, public official, military officer, or business executive you can. ALSO...get them from fellow investigators...IE...if Rob Lee, Harlan Carvey, and say...Jesse Kornblum say...hey...this guy is legit, then chances are that is going to carry a lot of weight with any respective PD.
4. Be an effective communicator. We deal with some of the most technical information in the IT world...and when on the stand, we may have to explain some of that highly technical information to a jury of our "peers"...which according to most PDs, is about as educated as the average 7th grader. So, know your audience...talk TO them, but never DOWN to them. Save the $5 words for the lawyers...remember the KISS pronciple on the stand.
ALSO...there is something I call the, "Your Mom" principle. If you can get your mom to understand (or some non-technical person provide your mom is either not around, or is in fact an IT engineer as well), then you should be good to go. Remeber, the goal is to convey the "story" of what happened...without spin...to the jury, not impress them with how smart you are.
Again, Kudos to Rob Lee and the SANS Institute for putting on yet another fantastic conferece. I said this last year, and I will say it again...if you only have the funding for one conference per year, THIS IS THE ONE to attend. There are more expert speakers, more potential to make great contacts, and more opportunity to learn at THIS conference, than any other confernce I have attended or spoken at! Great job ROB!!!
Monday, June 21, 2010
B-SIDESLV 2010
Going to be at the 2810 Vegas Estate...Not too shabby!

Timeline Spikes
Well...here are the commands to parse your timelines to show you exactly that...
To see file system activity represented numerically:
Strings timeline
This command will show you the days of that month, sorted numerically, with a count of the number of hits on that day to the left. This will show both spikes and lulls as well as letting you get a feel for what “normal” file system activity looks like.
You can also see which files were created on a certain date:
Strings timeline
This command will show you all of the files “birthed” on that month. You can also drill down to the day by adding a grep for the specific day...which is actually easier since the format in the timeline is a contiguous
Strings
One thing that I have noticed in my experience with timelines is that nefarious activity (like file creations, and download activity) is that it occurs in clusters. When I review my timeline, I will see the bad guys dumping say three or four files onto the target system (usually in the %windir% or %windir%\system32 directories. So would this activity register as a spike in "normal" activity? What if you added the Event logs into the timeline with Log2Timeline? Would additional statistical information becmore more clear by simply looking at the numerical count for activity on a specific date?
I know that this is a really short blog post...sorry...been REALLY busy lately, but I hope that it shows you the possibilities that are available to you when you use the command line and your brain. Timelines are really really useful pieces of data!
Thursday, June 3, 2010
Friday, May 28, 2010
Case Notes
If you answered, "What's Case Notes?", let me splain.
Case Notes is an awesome tool for taking notes during your investigations. Unlike simply using Notepad or Word Pad, Case Notes timestamps your entries, allows you to password protect your notes file, has customizable tabs, and keeps creates an audit log of your activity.
Once you download and install CN (either 32 or 64 bit version) you are prompted to set up your preferences...like this...

As you can see, I can set up to 10 fields of metadata such as my name, my agency, the case type etc...very handy. Then you can customize up to four (4) additional tabs for specific notes. The main space for notes is a tab called, "Case Notes" and cannot be changed. You will also have a tab labeled, "Audit Log" which also cannot be changed. So if you use all four like I did, you will have a total of six tabs.
I use my tabs to keep track of evidence items...systems, hostnames, IP addresses, etc, Dirty Words (keywords)...stuff I run across that I want to search for on my image(s), Questions that need to be answered and the subsequent answers, and my Investigation plan...what am I trying to accomplish, and why.
So, once you are all set up, your screen will look like this...

Now that we have covered the tool, let's cover the concept.
Harlan and I were talking this morning and we were wondering why so many investigators don't create an investigation plan. I mean, it seems like a no brainer doesn't it. What are you looking for? What have you been hired to do? What is the overall purpose of the investigation? That would be the first thing you should write down.
Next, you can break the investigation into smaller, more manageable chunks that feed into the overall investigation plan. This is where you would use the Alexiou principle...
1. What question are you trying to answer?
2. What data do you need to answer that question?
3. How do you extract and analyze that data?
4. What does the data tell you?
Here is an example...
1. I want to know if the admin user account was used to launch malware.exe
2. I need the ntuser.dat file for the admin user
3. I am going to parse the MUICache and UserAssist Keys with Reg Ripper
4. The data from the UserAssist key indicates that malware.exe was launched by the admin user
This is pretty basic example, but it illustrates my point. You can ask yourself questions and answer them...inputting both into your case notes. Once you have your questions answered, you can update your investigation plan with HOW that information is relevant to the case.
For example, in this case what would the fact that malware.exe was launched locally by admin. Well, for one, I now know that the intruder had admin access. I also know that because the data appeared in the UserAssist key, that they had an interactive session with the shell. So what does that mean? Well, that means they had to login from somewhere, right? So now, I just generated some additional questions that need to be answered...so in my case notes, I would update my investigation plan and my To be answered sections.
1. How did the intruder gain admin access? I need to crack the passwords from the NTLM hashes and see what they are. I also need to parse the SAM hive to determine if the passwords were recently changed, and get the last login times for users in the admin group. If the passwords for admin users were changed recently, I need to get the passwords before the change. I can check to see if the system was taking restore points (or shadow volume copies) and extract the SAM and SYSTEM hives from the date immediately prior to the change. Then I can crack the NTLM hashes and get the passwords before the change occurred.
2. When did they gain access? I can tell this by looking at my timeline (which is one the FIRST things you need to create) and check the first appearance of malware.exe. That should give me a great place to start looking for remote access. I can then look for remote access attempts in the Security event logs. Does the customer have a VPN? Does it log? What about remote management tools? Which ones are in use (RDP, pcAnywhere, VNC, etc)? Are they open to the external internet? Do they log?
All of this from JUST answering a single question! Then as you progress through you case, if you take good notes you will make report writing MUCH MUCH easier! Also, since cases are getting more and more complex, and like me, you may be working more than one case at a time, good notes will keep you from trying to remember what you were doing three days ago and what you were thinking that made you do whatever it was that you were doing? Finally, should you get pulled off the case for any reason (or you just need help) good notes will help your fellow investigators know what you were doing, what you were thinking, and where you were headed.
So, back to my original question...if you are not using Case Notes...why? It's free. It's a great tool that has some really nice options. And taking good notes will help you keep your thoughts organized, and write your final report.
Lesson learned...TAKE GOOD NOTES!!!!!! I will give a dollar to anyone who can give me a good reason for not taking notes during a case. I am going to bet dollars to doughnuts that nobody is going to have any reason compelling enough for me to part with my GWs.
Happy hunting...and remember...TAKE GOOD NOTES!!!!
Wednesday, May 26, 2010
CyberJungle Interview

Tomorrow morning, I am going to be interviewed by Ira Victor for the radio show, The Cyber Jungle. He is going to be asking me about Sniper Forensics...what it is, what it means to investigators, and how using it can help you!
Listen in if you get the chance!
Tuesday, May 25, 2010
SANS What Works 2010

I will be delivering Sniper Forensics at the SANS What Works conference in DC on July 8th and 9th. Last year's conference was awesome, so I'm sure this year's will be even better. If you have some money budgeted for a conference this year, and can only pick one, this would be the one to attend!

Monday, May 24, 2010
Crack-a-Lacka
OK…so you may have heard that’s it pretty easy to crack SAM hives using tools like Cain & Able or Ophcrack, but, you have never done it before, you don’t know where to start looking, and you feel like a dolt. No worries my friend, I am here to help.
First, download Cain from Oxid.it, and Ophcrack from Sourceforge. These files WILL be identified as malware by your AV software, so make sure you drop them into a good tools directory that is not being monitored. Creating an exception for specific files and folders is a function most (if not all) current AV releases can do, and should be done if you are working in the incident response/forensics industry since you will likely have a slew of tools that would make most AV engines freak out.
Once you have your tools downloaded, use FTK lite and extract your local SAM and SYSTEM hives. While Cain will dump your NTLM hashes from you local system, I want to show you how to do this as if you were working on an actual case. I think it goes without saying that you would NEVER install Cain or Ophcrack onto a customer system...but there...I just said it now didn't I?

Next, I simply right click, and select “Export Files”. I drop them into a specific folder on my desktop, and I am ready to roll…go ahead and close FTK Lite at this point.
Next open Cain, go to tools, and select “Syskey Decoder”…like this…

From here, you will get a popup that looks like this…click on the tripe dots and navigate to where you dropped the system hive you just copied with FTK Lite.
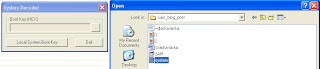
Once you click on the system hive, that little window under where it says, “Boot Key (HEX) will be populated with a long string of numbers and letters. Copy that to your clipboard as you will need it in the next step.
Now, select the “Cracker” tab, and click on the big blue plus sign that sits right beneath the “Tools” menu tab. Then navigate to the SAM hive you just copied using FTK Lite, and paste in the Syskey that you just copied to your clipboard…should look like this…

When you click “Next”, Cain will dump the NTLM hashes from the SAM hive. Your table will now be loaded with whatever user accounts are on that machine, along with the NTLM hashes.
Next, highlight whichever users you want to crack, right click, and select export. Save them to the same place you dropped your hives (for ease of use), and close Cain.
Now open Ophcrack. My .lc out put file, when I open it with Textpad, looks like this…
cepogue:"":"":E4C3436DDD1F625CEBB15F4C062DCC55:EC85B8E81AE28777453327655700B6AE
I am interested in this part only…
E4C3436DDD1F625CEBB15F4C062DCC55:EC85B8E81AE28777453327655700B6AE
THAT is the NTLM hash for the user account cepogue.
On Ophcrack, click “Load”, then “Sinlge Hash” and paste the NTLM hash you want to crack in the little window like so…

Click OK. Now simply highlight, and click “Crack”. In less than a minute, my password was cracked!

Blamo! Pretty slick huh (Yes…I changed my password for the purpose of this example)!
Now, notice that I have two little green dots at the bottom of my screen. Those indicate that I have The “XP Free Fast”, and “XP Free Small” tables loaded. These are free (as indicated by the name) and can be downloaded from the web. You can also purchase larger tabs, or create custom tabs for specific tables (like Rainbow tables, or tables you have created with a word permuter).
I pretty much do this on every case. It’s quick, and gives me a great insight into the security posture of my customer. If like the admin password is “password”, or the “sqldevadmin” password is “sqldevadmin”, I know I they were likely wide open at the time of the incident. If I can crack the passwords in under five minutes, so can the bad guys.
Also, don’t let the customer fool you and say, “oh…our passwords have ALWAYS been strong!”. Parse the SAM hive with Harlan’s RegRipper and look at the “PWD Reset Date” under that username. If it’s a recent date, A) Obviously they’ve changed it, and B) You can always go to the _system_volume_information and extract the previous SAM hive (provided the system is taking restore points or shadow volume copies. ) Then simply extract the previous SAM hive, and repeat the same steps outlined above. Once you get the previous password you can be all…dood…”You changed you password on THIS date (as evidenced by the SAM hive), and your previous password was THIS..as I was able to extract it from the previous SAM hive that I extracted from the restore point from the day before you changed the password…SUCKA!”
Happy Hunting!
